
Special note for those in higher education or who are using Zoom for business: Zoom is NOT compliant with the Family Educational Rights and Privacy Act (FERPA) colleges and universities are required to abide by to protect the personal information of students. The software is also not secure enough to be used for many businesses; Zoom should not be used to share protected health information (PHI) or to convey financial or other private consumer information as protected by the Gramm-Leach-Bliley Act (GLBA).
3 commonly asked questions about Zoom
As the coronavirus pandemic continues to sweep our nation, businesses and individuals are turning to video meeting software to replace various conversations and events that typically occur in-person. From virtual business meetings to game nights, cocktail hours and just about everything in between, now more than ever, millions of people are using virtual event platforms to connect with each other on a daily basis. One software, in particular, seems to be rising to the top of everyone’s inbox – Zoom.
Zoom, a virtual meeting software founded in 2011, is quickly gaining popularity among people all over the world. In fact, Zoom recently announced that their usual 10 million daily users skyrocketed to more than 200 million daily users in just a matter of weeks as stay home orders went into effect across the country. And now that they seem to be a household name for hundreds of millions of Americans and users all around the world, people are starting to ask questions about the security of Zoom’s platform.
That’s where I come in. As a department chair in Davenport University’s College of Technology, I was recently given the chance to talk about this very topic, Zoom security, on WOOD Morning News Radio. During the conversation, three particular questions came up that I wanted to answer in a little more detail than time allowed on-air.
First question: Is Zoom secure?
The simple answer to this question is no, at least not automatically. Let me explain.
Let’s first start by tackling my favorite conversation, “Zoombombing.” If you’re not aware of this term, it’s because it has recently risen to fame in just a matter of weeks. Zoombombing, similar to photobombing, is when an individual joins a live Zoom meeting completely unprompted and, most certainly, unwelcomed. While different “Zoombombers” seem to have their own, unique motives, if this new trend tells you anything, it should tell you that Zoom is not as secure of software as they may lead it on to be.
More so than just the latest trend of Zoombombing, Zoom claims to have end-to-end encryption across its software. Essentially, this means it would be impossible for the Zoom corporation or other third-parties to “spy” on meetings, its participants or the data collected from those meetings. However, this is where it gets interesting (especially for cybersecurity folks like me).
The end-to-end encryption that is heavily promoted by the organization only really seems to be in place when all meeting participants are logged in on their computer. As soon as someone calls into the meeting on their phone, it seems as though all bets are off. But it’s not as easy as just ensuring that no participants are on their phones because, from the sounds of it, even those meetings taking place only on computers can still be accessed by the Zoom service itself. So, it seems as if Zoom has its own meaning of complete “end-to-end encryption.” For these reasons, I would caution you to take Zoom’s security with a grain of salt.
While all of this sounds a little scary, there is no hiding the fact that Zoom has some really great features that a lot of other tools can’t compete with. Trust me, I get it – the customizable backgrounds are cool. That’s why I want to dive deeper into how to make your next Zoom meeting a little more secure if you insist on using the software for its set of advanced features.
Second question: If I still want to use Zoom, is there anything I can do to make my meetings more secure?
Yes, there are a number of settings pre-built into Zoom that will drastically reduce your chances of having an individual hack or join in on your next important meeting. Here are some of them:
- Disable “one-click join” – automatically enabled
Zoom, by default, now requires passwords for scheduled meetings – which is great. However, what it doesn’t automatically disable is the ability to embed a “one-click join” link in email invites. Basically, defeating the entire purpose of the password in the first place because if clicked, the link won’t require a participant to enter a password. So, the first thing I’d recommend to any future Zoom host is that you disable the “Embed password in meeting link for one-click join” to ensure that no matter how a participant gets your meeting ID, they must first enter a password to be let into the meeting.

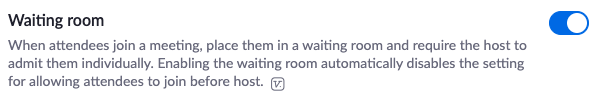
- Set up a waiting room – automatically enabled
The second thing I recommend you do is enable the “waiting room.” Zoom recently adjusted its default setting to automatically enable this feature on most accounts, but it’s still worth double-checking your settings. This feature makes it so that the host has to accept everyone into the meeting. That way if the host doesn’t recognize someone trying to join the meeting, it’s as simple as not letting them in. Pretty nice feature, right?
- Disable screen sharing setting, if possible – automatically enabled
In some meetings, participants are asked to share their screen with recent research, their new project idea or anything in between those two. But, if that’s not the case and you’re only utilizing the tool to talk or run a meeting, I recommend you disable this setting on the off chance that your meeting experiences an unwelcome visitor.

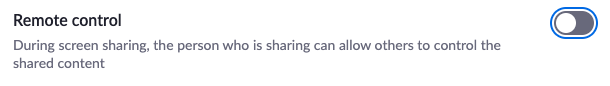
- Disable “remote control” – automatically enabled
This is another feature that, for some reason, is automatically enabled by Zoom. The feature essentially allows a participant to control the screen of someone sharing their content with the group. Yikes!
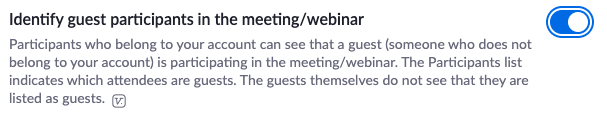
- Identify guests – automatically disabled
This feature is also one that is automatically turned off by default and mainly applies to businesses that are using Zoom for group meetings. If you enable this feature, it will automatically alert the group when someone outside of your own organization joins the meeting. It’s an especially useful function if you’re not expecting anyone outside of your own team to join a meeting.
Third question: Is there another, better video conferencing software I should be using instead of Zoom?
The simple answer to this question is yes. There are a number of video conferencing platforms available and more that seem to be popping up by the day.
For businesses, I recommend using your built-in software that comes with your email platform – typically either Google Hangouts Meet or Microsoft Teams. Both of these are great options for businesses because they are typically already part of your organization’s technological infrastructure, supported by your team’s IT department and require no additional funding. If those aren’t an option for your business or aren’t pre-built into your organization, I also really like Cisco Webex because, unlike Zoom, it runs on its own protocol standards and tends to be less vulnerable to hackers around the world. In recent weeks, Cisco has also beefed up the features of the free version of Webex to help schools and businesses securely transition to video conferencing.
For individuals, my two favorite video conferencing platforms are FaceTime and Signal. FaceTime uses true end-to-end encryption which means that no one, and I mean no one, can access your chats – not even Apple. Signal is also supported by true end-to-end encryption which is why I enjoy it for security reasons. However, it does lack some functionality in the fact that it’s not made for big group chats, it’s mainly used for private, one-on-one conversations.
Now that I’ve listed those and expressed some security concerns, I would be remiss if I didn’t expand on one of my points above and say that Zoom continues to update its privacy policy and default meeting settings regularly. So, while yes there is other software I recommend, if you’re looking for functionality over security, Zoom should not drop off your go-to virtual meeting platform list. If you do decide to continue using it, I would just recommend that you first adjust some of your settings in order to better protect yourself and your organization.



No Responses